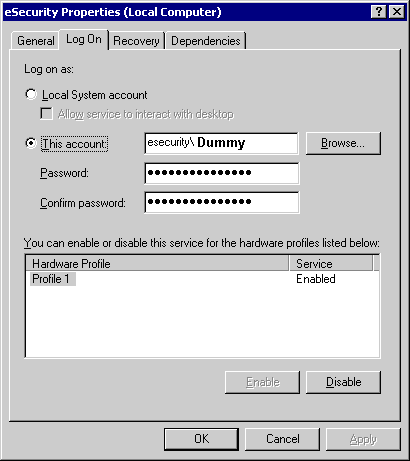
mpgn on X: "From nt authority\local (or network) service to nt authority\ system ⚔️ 1⃣ Shell as nt authority\local service / network 2⃣ Run FullPower from @itm4n ✓ Getting SeImpersonatePrivilege to enabled 3⃣
![Solved]The Computer account 'DAG' could not be validated. Access was denied. Check that the current user (NT AUTHORITY\SYSTEM) has permissions to create computer accounts in the domain or to claim the computer Solved]The Computer account 'DAG' could not be validated. Access was denied. Check that the current user (NT AUTHORITY\SYSTEM) has permissions to create computer accounts in the domain or to claim the computer](https://pdhewaju.com.np/wp-content/uploads/2017/01/123116_1904_SolvedTheCo2.png)
Solved]The Computer account 'DAG' could not be validated. Access was denied. Check that the current user (NT AUTHORITY\SYSTEM) has permissions to create computer accounts in the domain or to claim the computer
![DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog](https://sqlbackupandftp.com/blog/wp-content/uploads/2018/06/Map-User-to-Database-step-2.png)
DBMS-MSSQL:11006#916] The server principal “NT AUTHORITY\SYSTEM” is not able to access the database under the current security context | SQLBackupAndFTP's blog

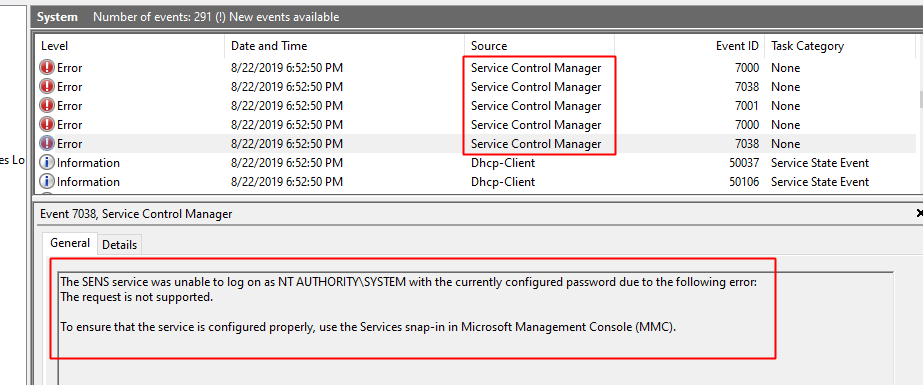
Event Log Error: NT AUTHORITY\SYSTEM is not setup for single sign-on - ERP 10 - Epicor User Help Forum

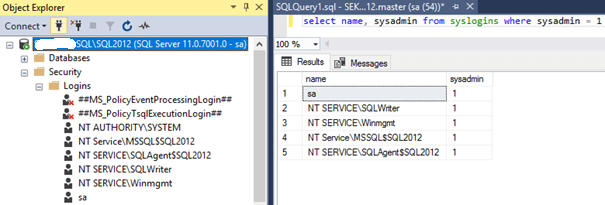
Unable to revoke permissions for 'NT AUTHORITY\SYSTEM' on SQL Server 2016 - Database Administrators Stack Exchange

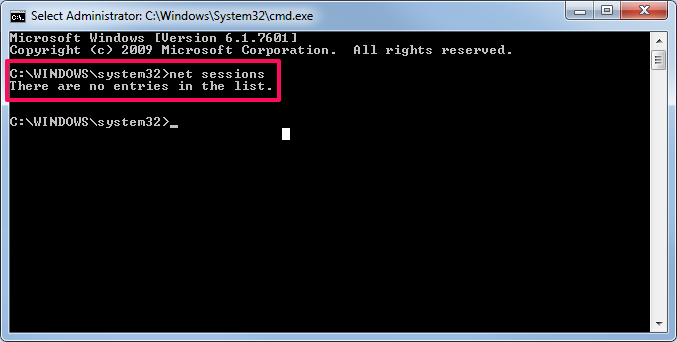
windows server 2003 - Why process running as Local System accessing a UNC share being seen as NT AUTHORITY\ANONYMOUS LOGON? - Server Fault
![KB8406] Add permissions to get database data locations to generate automatic exclusions for Microsoft SQL Server in ESET Windows server products KB8406] Add permissions to get database data locations to generate automatic exclusions for Microsoft SQL Server in ESET Windows server products](https://support.eset.com/storage/IMAGES/en/11983_KB8406/KB8406Fig1-1.png)
KB8406] Add permissions to get database data locations to generate automatic exclusions for Microsoft SQL Server in ESET Windows server products
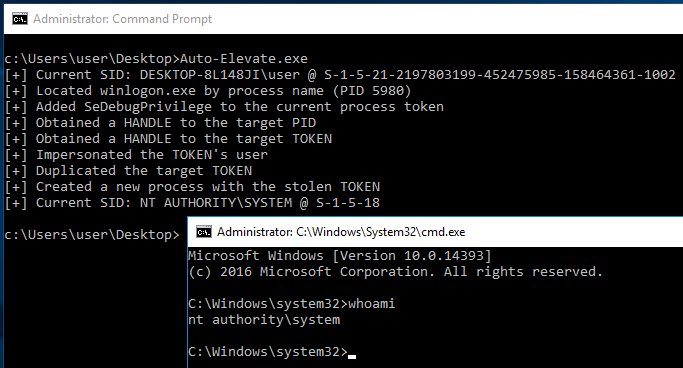
GitHub - FULLSHADE/Auto-Elevate: Escalate from a low-integrity Administrator account to NT AUTHORITY\SYSTEM without an LPE exploit by combining a COM UAC bypass and Token Impersonation