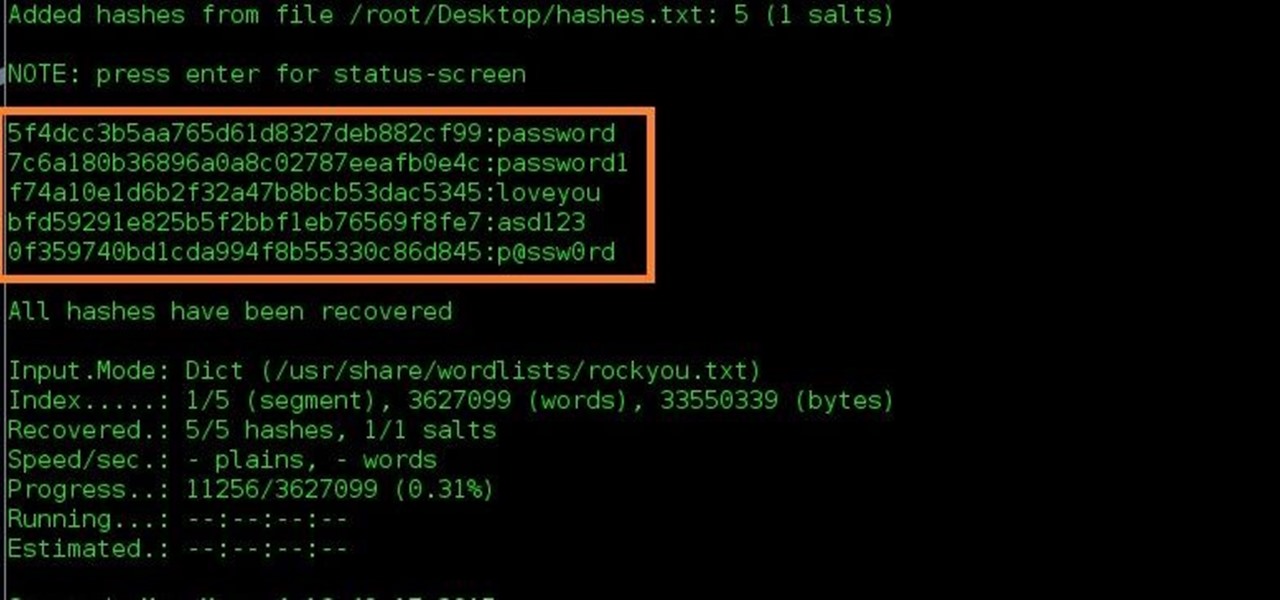
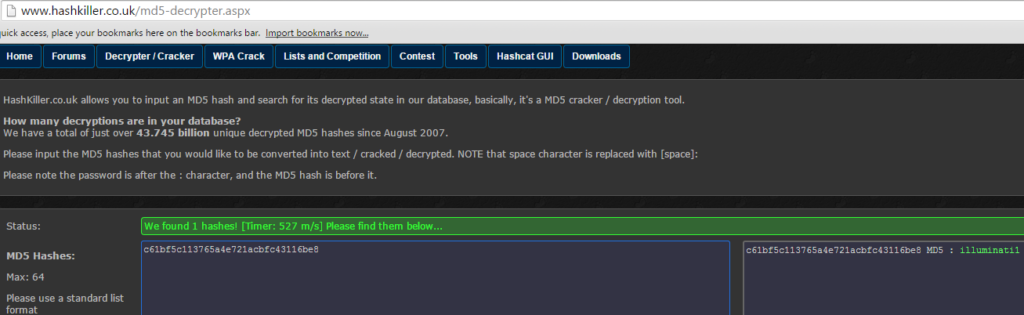
KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Cyber University of the year: Four years running: 2019, 2020, 2021, 2022
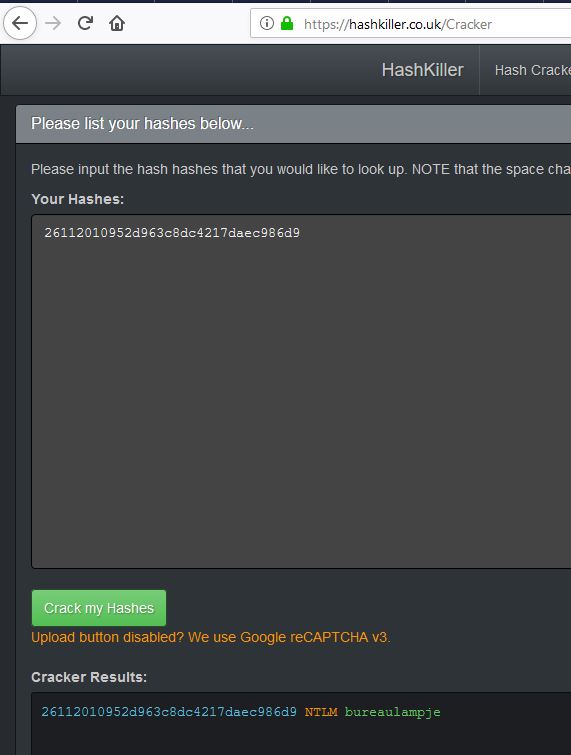
Malware analysis https://hashkiller.co.uk/ntlm-decrypter.aspx Malicious activity | ANY.RUN - Malware Sandbox Online





![Hashkill 0.3.1] Password Cracker Tool Released Hashkill 0.3.1] Password Cracker Tool Released](https://1.bp.blogspot.com/-O1NukABHlPk/UR5psXWGd_I/AAAAAAAAUhM/0D34wxep8qQ/s1600/Password+Cracker+Tool+Hashkill+version+0.3.1+released.png)