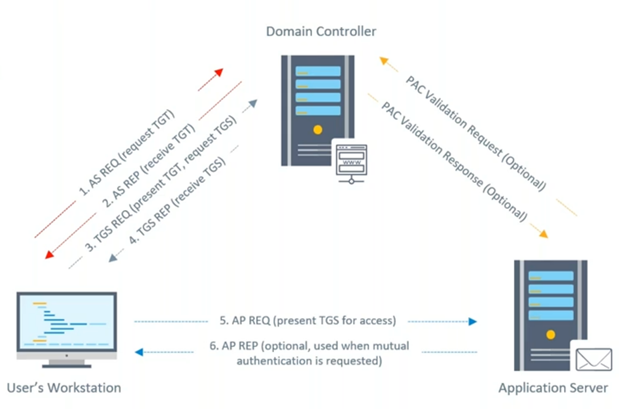
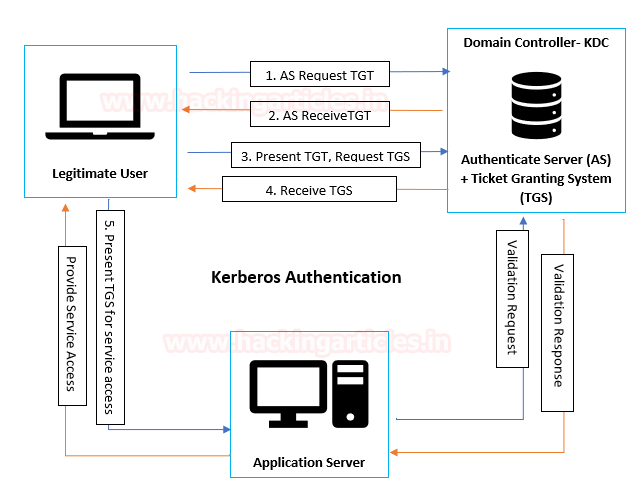
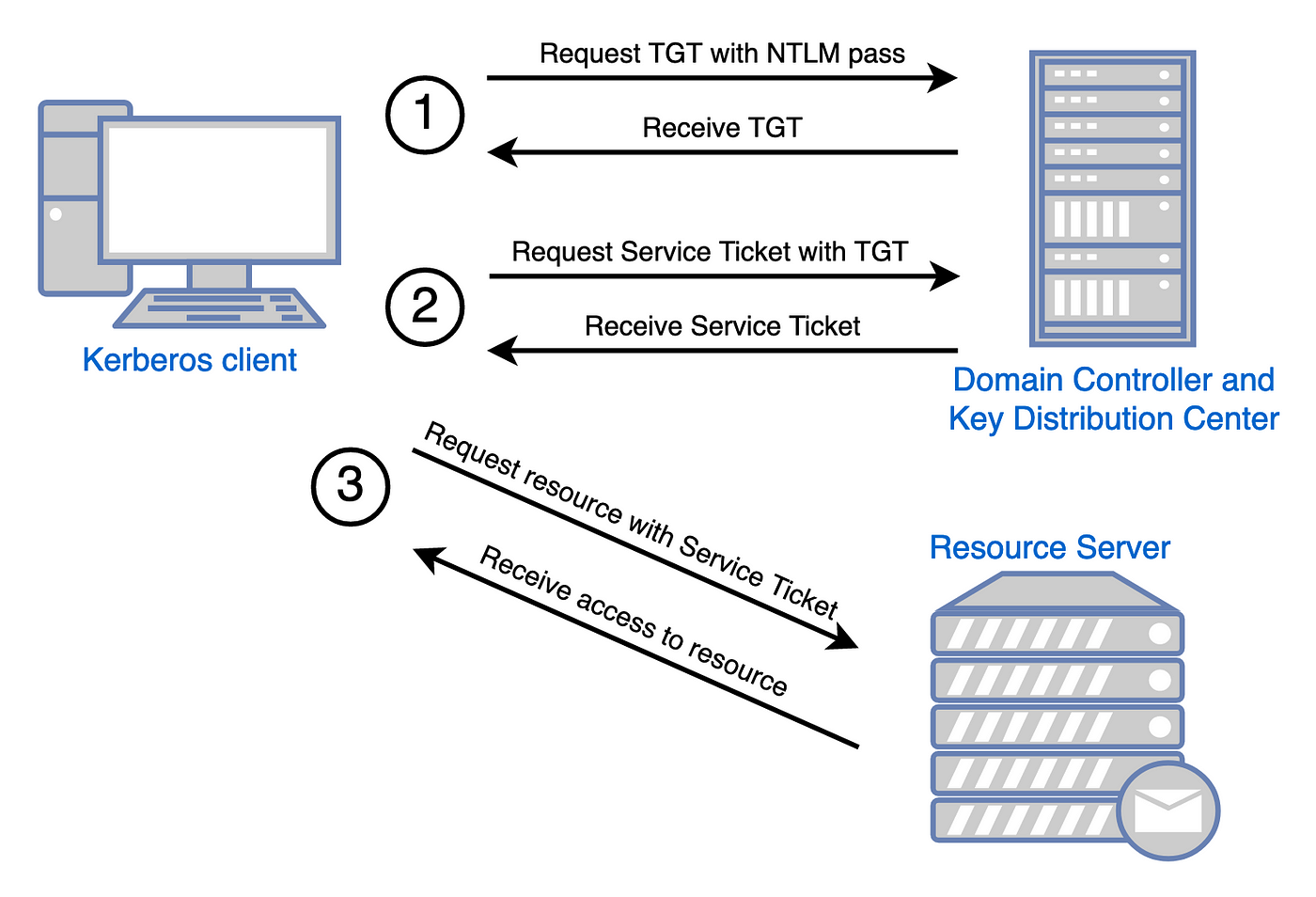
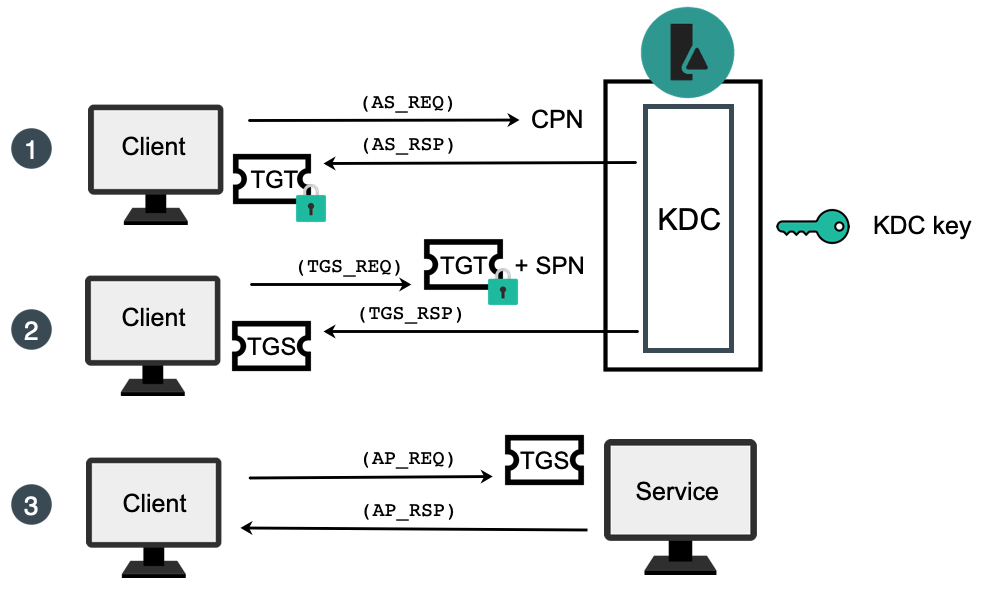
Ptrace Security GmbH on X: "How to Golden Ticket Attack Active directory https://t.co/UlSE6KoMw4 #Pentesting #Windows #ActiveDirectory #CyberSecurity #Infosec https://t.co/b7REKzcgYc" / X

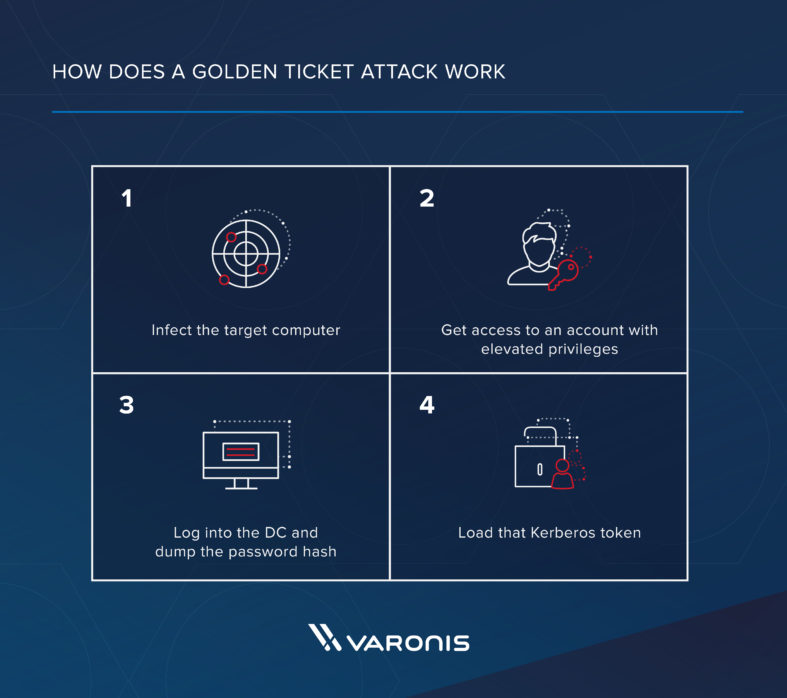
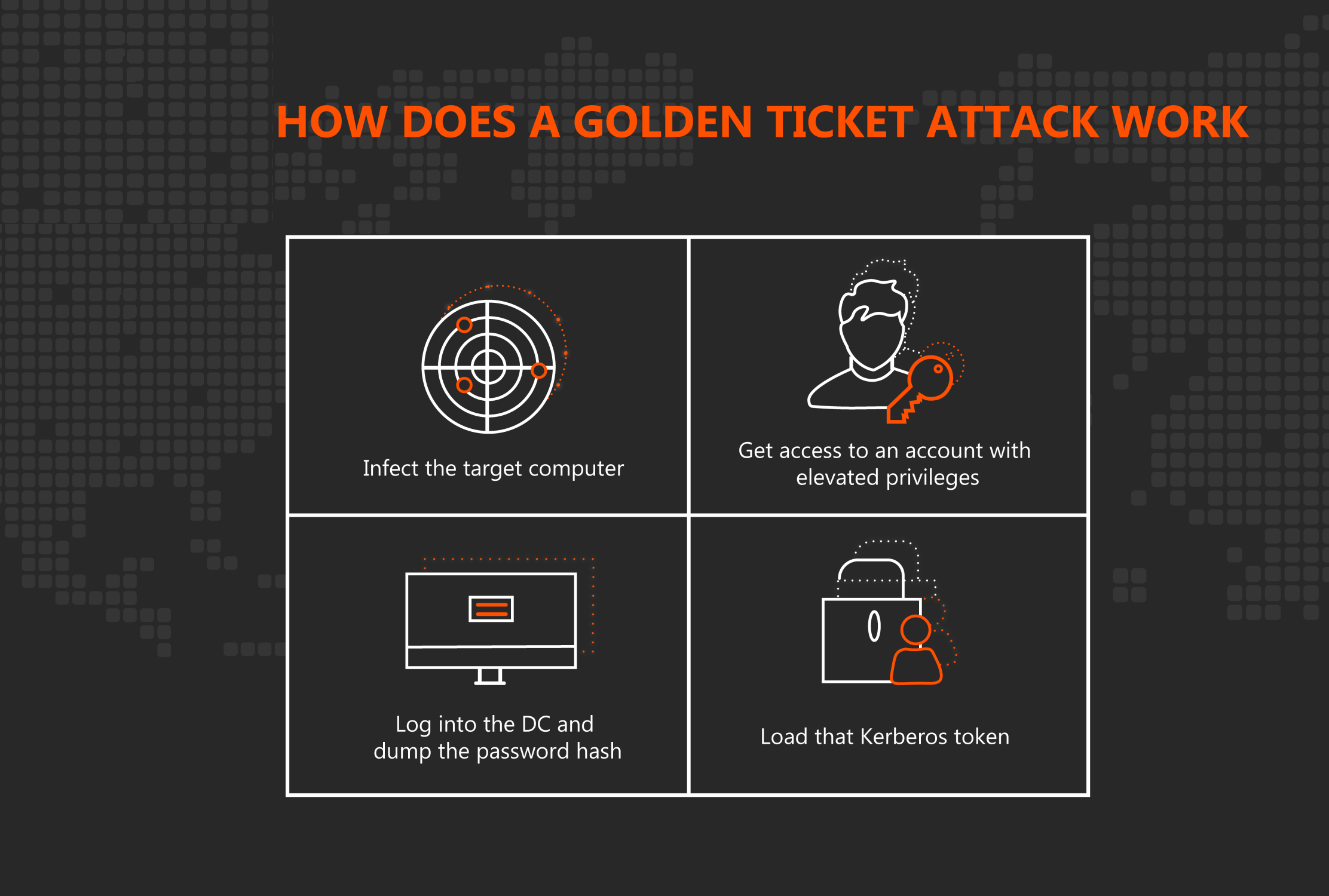
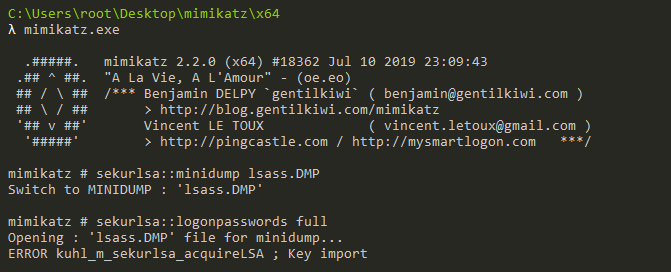
How Kerberos Golden Ticket Attacks Are Signaling a Greater Need for Identity-Based Security - SentinelOne
How Kerberos Golden Ticket Attacks Are Signaling a Greater Need for Identity-Based Security - SentinelOne
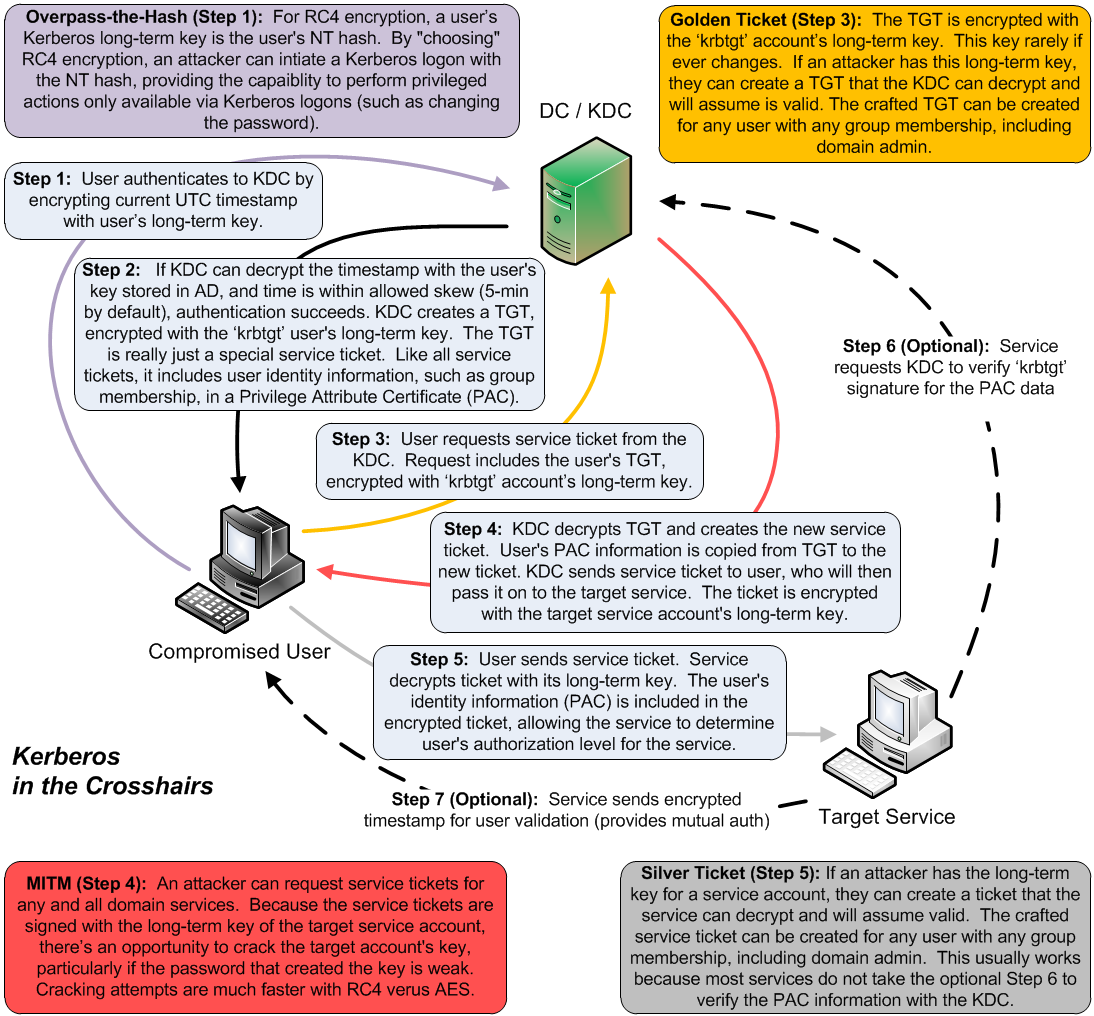
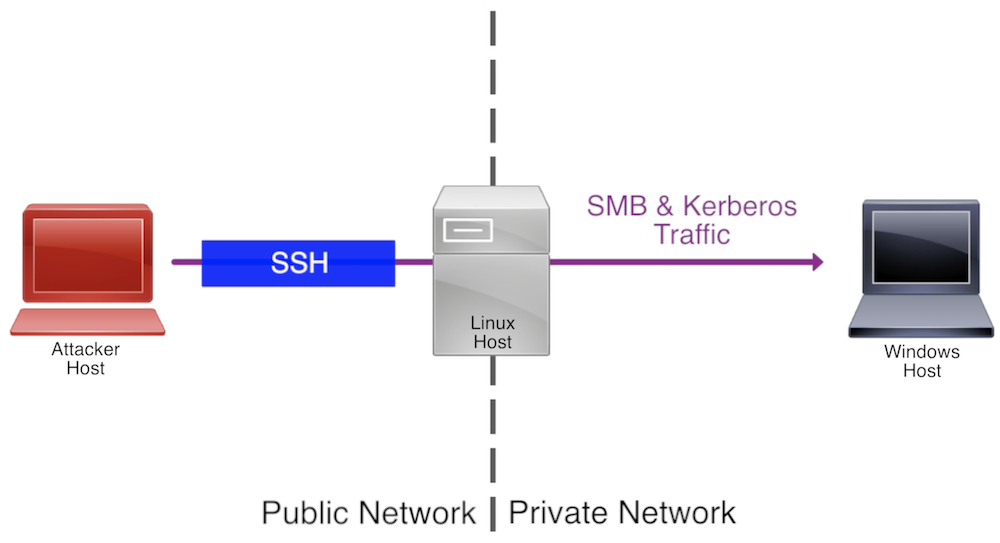
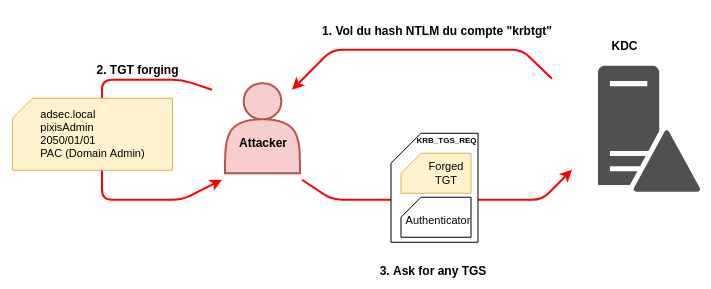
SANS Digital Forensics and Incident Response Blog | Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More | SANS Institute
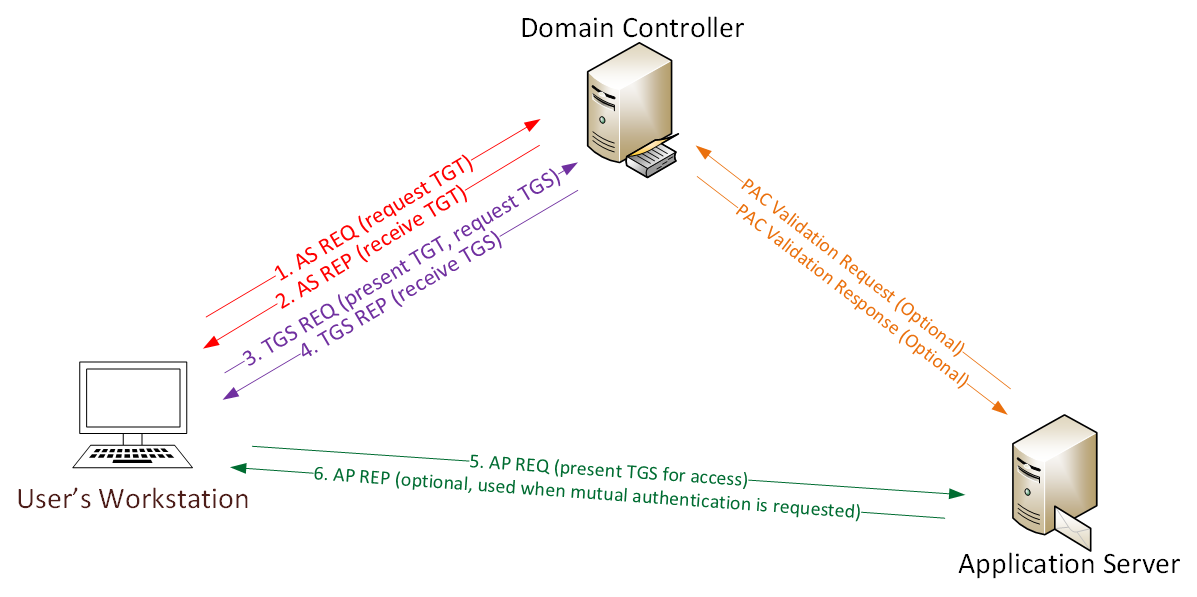
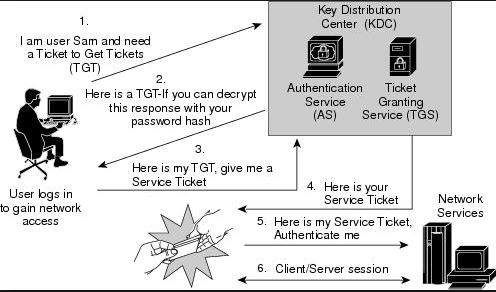
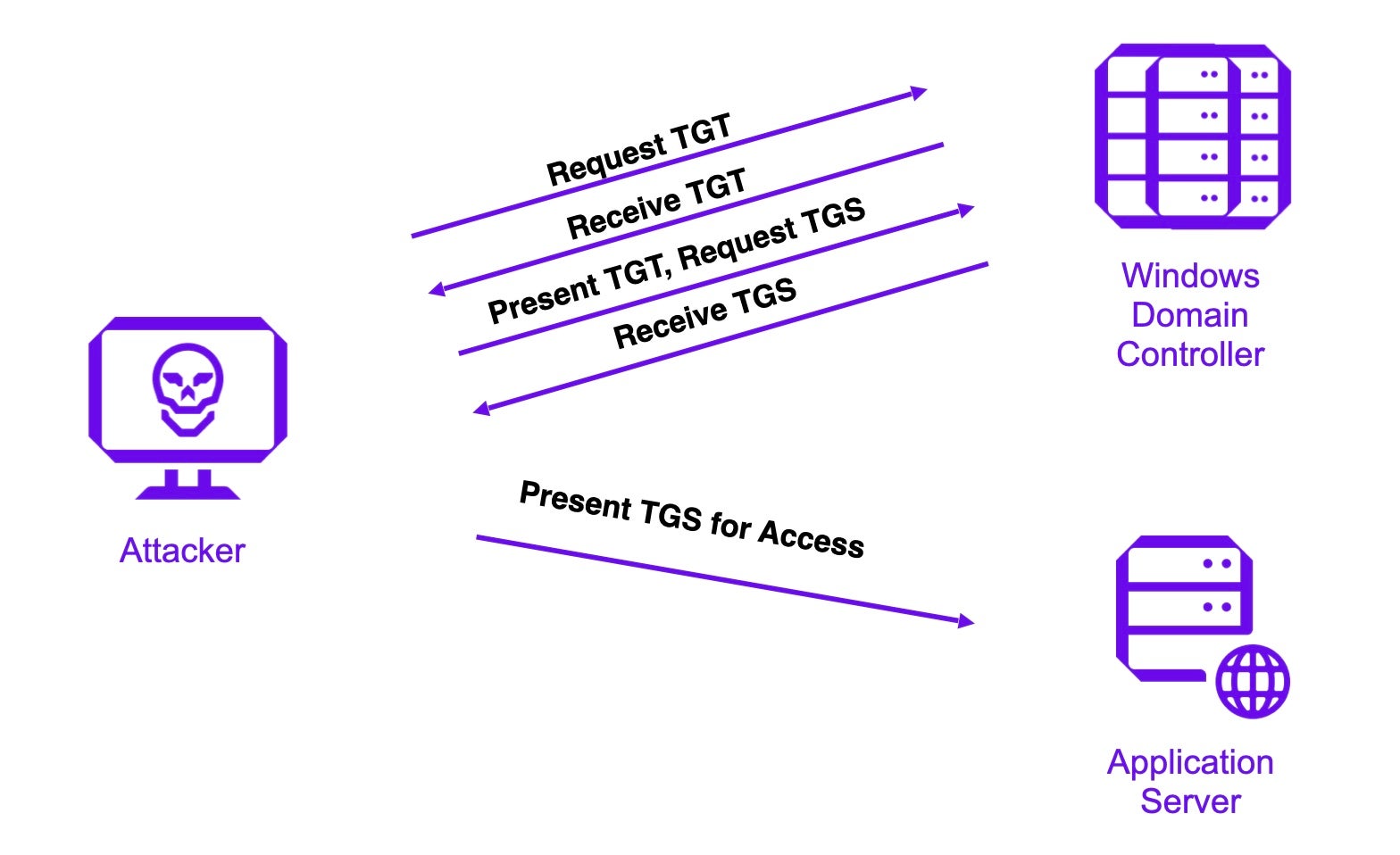
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory » Active Directory Security