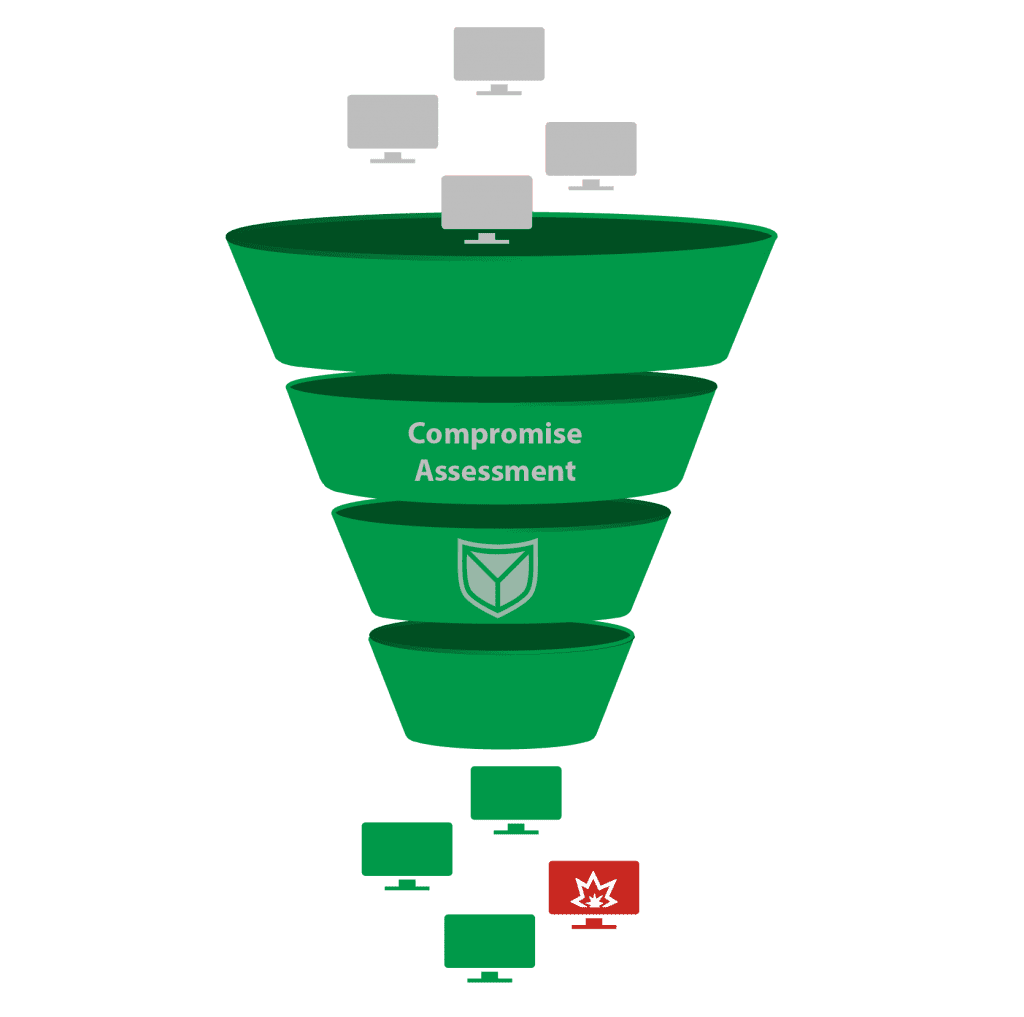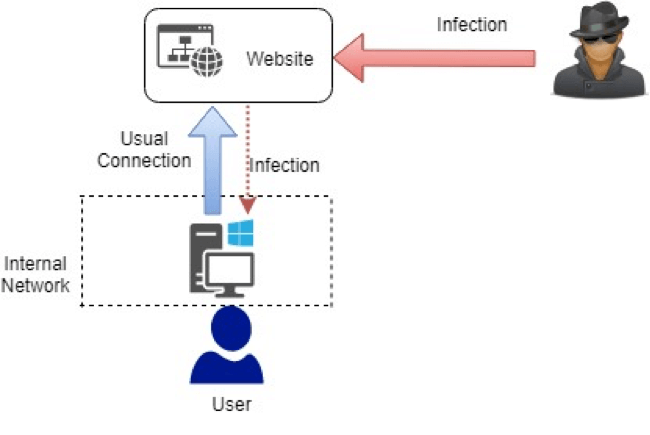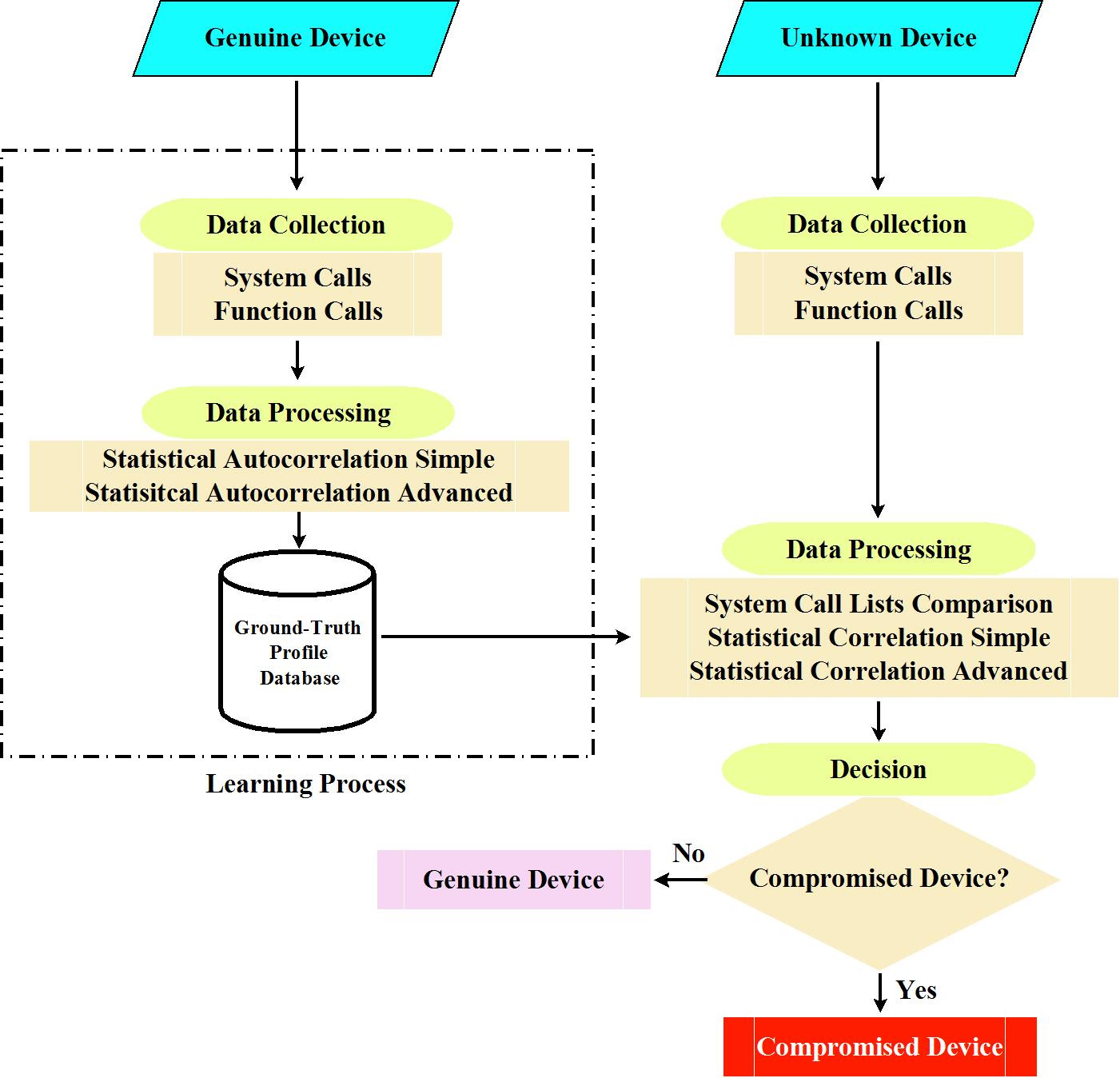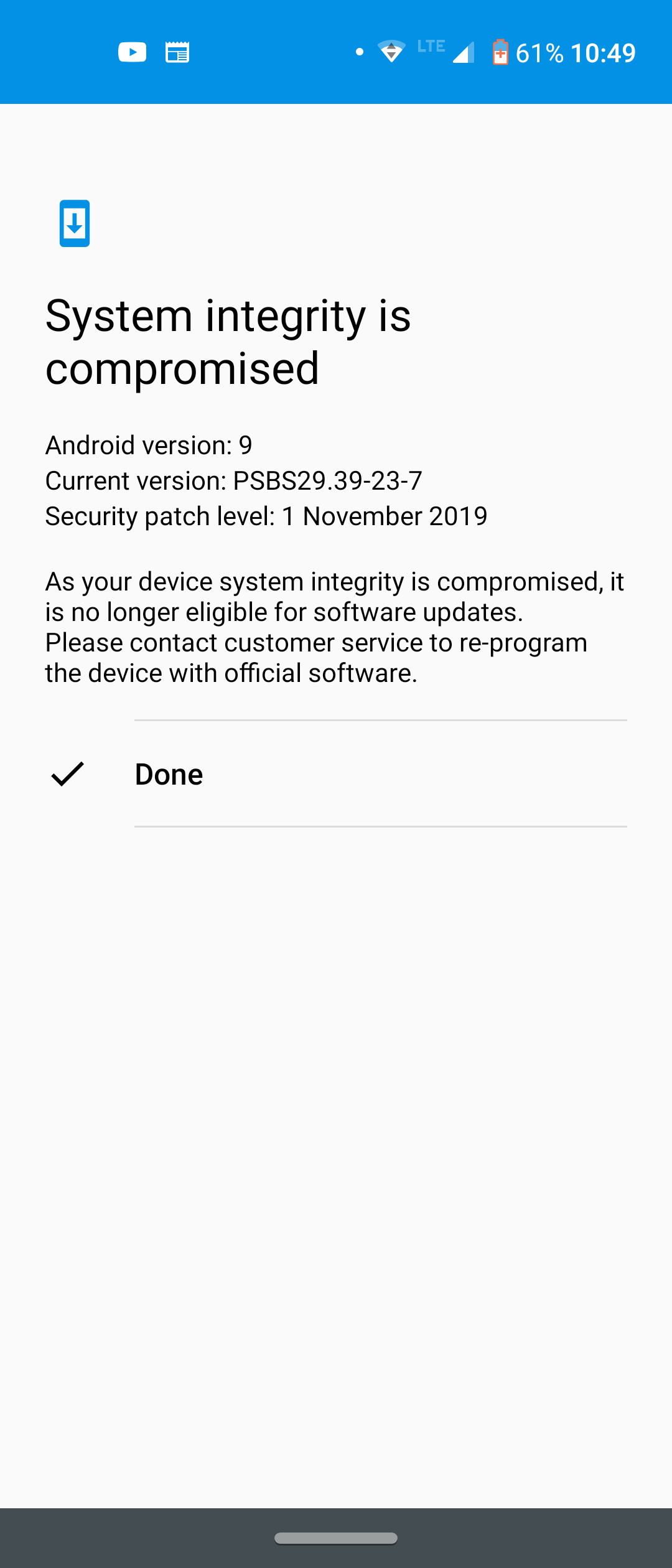
System-Integrity-is-compromised-Is-it-due-to-unlocked-bootloader - English Motorola - MOTO COMMUNITY

System hacked warning alert on notebook (Laptop). Cyber attack on computer network, Virus, Spyware, Malware or Malicious software. Cyber security and cybercrime. Compromised information internet. Photos | Adobe Stock